Preparing for an information security assessment is a daunting challenge – especially if previous assessments were not handled well. In most cases, adequate preparation and a mindset geared towards getting an honest assessment of the current state will yield significant benefits for the organization only if sufficient effort is spent on delivery.
Great teams sometimes fail because of a lack of delivery management. This is as true for an information security assessment as it is for a development project. In fact, some may argue that it is truer of an assessment because of the finality and timing of the final report versus the iterative nature of many development projects. As the project manager for a recent information security assessment for a large healthcare organization, I wanted to share several best practices organizations should consider before planning an information security assessment.
Understand the driving force behind the assessment
It is crucial to understand why an assessment is required. Is it to support an internal review of a corrective action? Is it to assess progress since a previous assessment? Is it a compliance requirement? Is it to gain a general understanding of the organization – i.e., what standards it is (or is not) following, how efficient are the processes, etc.? Understanding why the assessment is important to the organization will help the stakeholders better prepare for it.
In my recent project, the organization needed to complete an assessment to validate the progress since a previous assessment. In this case, the previous assessment’s report became the baseline for the new assessment. The focus was on validating progress since the last assessment, confirmation that the target state (as defined during previous assessment) was still valid, and quantifying the organization’s improved information security posture.
Appoint a project manager and select a firm that will provide action-oriented feedback and guidance
Most audit firms with an information security practice have the appropriate knowledge to assess an organization’s information security programs based upon existing standards and guidelines (Figure 1 below). However, it is common practice to use junior consultants to meet with individual stakeholders and consume a lot of information in a short period of time, complete checklists, and draft reports for review and sign-off by the in-house experts. In these situations, the junior consultants are acting as both the coordinator and the assessor.
Figure 1 – Typical Assessment: Large Firm with Junior Consultants and No Project Manager Assigned

The typical approach poses the following shortcomings:
- Consultant focus is divided among coordination, collection, and assessment
- Interviews crammed into a short on-site timeframe are the primary source of information for the assessment
- Key stakeholders may not be available during the onsite assessment activity
- Consultants do not have expertise to probe or interpret deviations from the expected
In many cases, the senior experts sign-off on the results reported by junior consultants following the process they were directed to follow. The sign-off is essentially a verification that, based upon the documentation prepared by the assessor, the conclusions / findings are valid. However, if the documentation prepared by the assessor is misinterpreted, incomplete, or just plain wrong the report is useless. The lack of an accurate report leads to an ongoing costly effort of follow-up, clarification, and multiple draft versions of the final report.
Because no two organizations are exactly alike, organizations benefit the most when they assign a dedicated project manager to prepare the assessor and the internal stakeholders for the assessment and to guide senior level information security experts during the actual onsite assessment (Figure 2 below). In this scenario, the project manager sets the assessment plan with the assessor in advance and then works with stakeholders prior to the onsite assessment to prepare artifacts that evidence the organization’s information security posture.
Figure 2 – Recommended Assessment: Expert Information Security Consultants and Project Manager Assigned
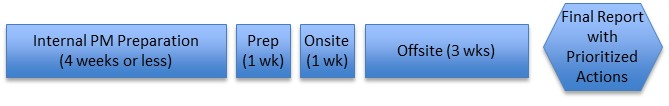
Assigning a project manager provides many benefits throughout an assessment including:
- The opportunity to understand (in advance of the assessment) the baseline requirements and work with all stakeholders (including assessor(s)) to identify framework, approach, and appropriate artifacts to support the assessment
- The ability to provide evidence to assessors in advance so they can prepare interview requests / questions and get better value out of their time onsite;
- The capacity to facilitate review of materials and answer questions (during the onsite assessment) as they come up will reduce the overall time commitment from all stakeholders
- The competence to facilitate review and plan implementation (following the assessment) of action-oriented assessment recommendations
Now that we’ve covered the first few best practices to a meaningful information security assessment by truly understanding the ‘why’, dedicating a project manager, and identifying the assessment firm – the real preparation work is ready to begin. Consider this the foundation to a successful assessment. I will reveal the remaining best practices for framing and finishing the assessment in Part 2 of this series coming soon.



